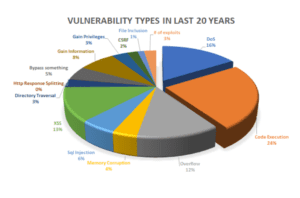
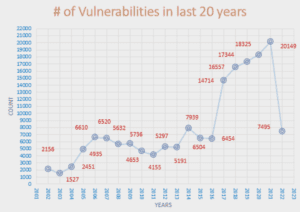
Cyber Security
About Us
Paradigm Infotech, Inc Managed Security Services delivers a diversified and customizable set of strategic and adaptive cybersecurity services that address the entire security landscape. These services include assessment and planning, SIEM management and security monitoring, perimeter and endpoint protection and incident response.
ParadigmIT has worked with many companies to make informed business decisions that ensure operational effectiveness is considered in the design, implementation, and management of their cybersecurity posture.




Why Us?
We do more than find and alert on threats. We have the experience and skills to deliver IT solutions for complex cybersecurity problems so your IT team or managed service provider (MSP) can easily and quickly implement changes to reduce overall risk while maintaining focus on business-critical tasks.
Our Services
FAQ's
As per CISA (Cybersecurity and Infrastructure Assurance Agency) from US Govt.: “Ransomware is an ever-evolving form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. Ransomware actors often target and threaten to sell or leak exfiltrated data on authentication information if the ransom is not paid.”
In the recent past most of the government websites and the users are being targeted by the ransomware attackers. It is being observed that, the attacks may not be always for personal interest, rather it may lead to an organized data collection task group.
There are good number of Ransomware making rounds in the industry. Few to list are
| Bad Rabbit | Cryptolocker | GoldenEye |
| Jigsaw | Locky | Maze |
| NotPetya | Petya | Ryuk |
| Wannacry |
Log4Shell is a severe, critical vulnerability affecting many versions of the Apache Log4j application. This vulnerability allows unauthenticated remote code execution. Log4Shell vulnerability is found in products of some of the most common technology vendors such as AWS, IBM, Cloudflare, Cisco, iCloud, Minecraft: Java Edition, Steam, and VMWare.
Log4j is critical it assessed that, most of the day-to-day applications are developed using Java and they will be vulnerable. Globally it is going to affect approximately 2.5 – 3 billion devices. Hence, it is very crucial for us to mitigate the risk.
Current mitigation is to remove JNDI Class files (Version 2.x), by replacing or removing references to context lookups (Version 2.x) and by removing JMSAppender for 1.x versions.
Please feel free to reach us at ask@paradigminfotech.com
Our analysts provide 24/7/365 monitoring of your network and assets in real-time and notify you of potential security notifications and potential security events